The office is unattended after work, and valuables such as computers, printers, and photocopiers in the office are attracting the attention of thieves. The number of security guards in property management is limited, and there is no way to monitor all offices at all times. The traditional video surveillance has become a hindrance. After discovering the theft, it is necessary to check the video. The thieves have already escaped. Use the Internet of Things technology to effectively solve the problem of burglary, initiate an alarm when the theft occurs, and notify the security guard to hunt.
Application requirements
Office fixed asset security management system
Figure 1 Product schematic
As shown in Figure 1, the anti-theft base station is installed at the entrance and exit of the office, and the anti-theft tag is bound to the valuables by means of pasting, and the remote control can be used to disarm and disarm the site.
1. Theft occurs, immediately alert
When the item that installs the mobile anti-theft tag is illegally taken out of the office, or the tag is violently removed, the anti-theft monitoring base station will issue an audible and visual alarm, and upload the alarm information to the system to notify the management personnel to check by SMS or telephone. Items that have a fixed anti-theft tag are triggered as soon as they are moved/lifted.
2. Fixed assets inventory
The system will check the fixed assets in the office once a day. If there is no report for 24 hours, the system will display an alarm on the system and notify the management to check the item.
system introduction
Figure 2 System topology
As shown in Figure 2, the monitoring base station is responsible for receiving the signal sent by the monitoring tag and uploading it to the server through the 3G network. Whenever and wherever, the administrator can access the server through the computer or mobile phone to achieve remote monitoring.
1. Mobile anti-theft tag
As an "electronic ID card" for anti-theft items, the mobile anti-theft tag has the characteristics of small and easy-to-use, adopts environmentally friendly low-power design, has a continuous service life of more than 2 years, and uses a dedicated frequency band, which is not susceptible to interference.
Figure 3 Schematic diagram of the exit alarm or disassembly alarm
As shown in Figure 3, the mobile anti-theft tag is mainly used for binding fixed assets that are moved indoors, such as office chairs, portable instruments (oscilloscopes, voltmeters, etc.). As shown in Figure 3, in the armed state, an alarm is triggered when the item is taken out of the door. At the same time, if the tag is violently disassembled by the thief, the tag will send an alarm signal to the anti-theft monitoring base station to trigger an alarm.
Figure 4 mobile anti-theft tag
As shown in Fig. 4, the mobile anti-theft tag has a size of 70.0 mm * 44.0 mm * 9.0 mm. The mobile anti-theft tag is attached to the surface of the article with a strong foam double-sided tape.
2. Fixed anti-theft tag
As an "electronic ID card" for anti-theft items, the fixed anti-theft tag has the characteristics of small and easy-to-use, adopts environmentally friendly low-power design, has a continuous service life of more than 2 years, and uses a dedicated frequency band, which is not susceptible to wireless interference.
Fixed anti-theft tags are mainly used for binding fixed assets that are not moved indoors, such as printers, computer mainframes, computer displays, photocopiers, projectors, etc. In the armed state, an alarm is triggered when the item is moved.
Figure 5 fixed anti-theft tag
As shown in Fig. 5, the fixed type anti-theft tag has a size of 70.0 mm * 44.0 mm * 9.0 mm. The fixed anti-theft tag is attached to the surface of the article with a strong foam double-sided tape.
3. Anti-theft monitoring base station
Office fixed asset security management system
Figure 6 anti-theft base station and installation instructions
As shown in FIG. 6, the anti-theft monitoring base station is configured to receive an alarm signal sent by an anti-theft tag in the office and perform an acousto-optic alarm, and upload it to the background server through the 3G network. As shown in Figure 7, the anti-theft monitoring base station needs to be installed at the office entrance and exit, and can be installed by bracket or ceiling. Anti-theft monitoring base station appearance size: 200mm (diameter) * 35mm (height).
4. Remote control
Figure 7 remote control
As shown in Figure 7, the remote control is used to arm, disarm, and stop the alarm. The remote control uses a dedicated frequency band and is immune to wireless interference. The remote control is powered by two 7-cell batteries, and the external dimensions are: 90mm*38mm*22mm.
5. Active card issuer
Figure 8 active card issuer
As shown in FIG. 8, the card issuer is connected to the computer through the USB interface, and the ID number of the anti-theft tag is read through the non-contact mode, and the administrator inputs the specific installation position of the anti-theft tag into the system, and binds with the ID number of the anti-theft tag. After the label housing is marked, the card issuance is completed. The card issuer can repeatedly issue the anti-theft tag for easy reuse. Appearance size: 145mm × 93mm × 35mm.
Software effect
1. Login interface
Figure 9 login interface
As shown in Figure 9, the user can enter the management system through the browser and enter the account password to log in to the system.
2. Device entry
Figure 10 Device entry
As shown in Figure 10, before installing the label, you need to enter relevant information in the system, such as the item name, office number, item number, etc., to identify and identify the label.
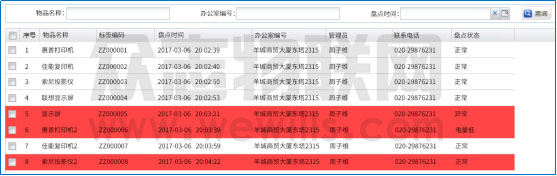
3. Equipment alarm
Figure 11 Device alarm
As shown in FIG. 11, when the anti-theft tag issues an alarm signal, the background system immediately displays the position and label of the alarm tag in the pop-up window at the lower right corner of the window, and the underlying color of the alarm record is marked in red, marking the unprocessed alarm information.
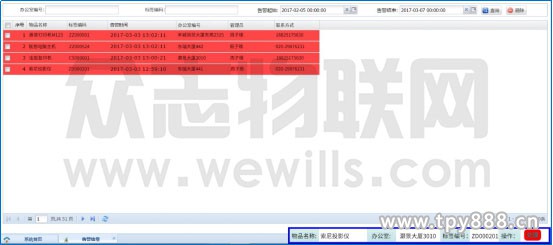
4. Device inventory
Figure 12 Device inventory
As shown in FIG. 12, the system can query the inventory information record, and the underlying device record base color is red.
Advantage highlight
1. Go to the dead angle coverage
The anti-theft base station accurately covers every position in the office, fully reducing the situation that the dead angle can not communicate, and making the anti-theft alarm more sensitive.
2. Label anti-disassembly
Labels are highly binding to valuables and are violently dismantled by thieves and alert.
3. Remote management
The management system accesses the Internet through the 3G network, and the management personnel can log in to the management system through the computer or mobile APP anytime and anywhere to perform remote monitoring.
4. Small radiation impact
Relative to the passive tag, the active tag can provide energy by itself, and the transmission power of the monitoring base station and the monitoring tag can be made very small, which is about one tenth of the radiation of the mobile phone.
5. Long working hours
The monitoring tag uses a low-data, low-power wireless technology that can work for long periods of time and can last up to 2 years.
Hand Pads And Roll
Non-woven abrasive scouring pad roll is made from high quality nylon fibre.
Bonding abrasive on the non-woven with special resin. It's with high flexibility.
Industrial scouring pads are mainly used in the coating treatment of the surface of metal, wood and other materials, mechanical maintenance and cleaning such as cleaning, polishing, rust removal, deburring, and high-quality appearance decoration line processing operations.
The characteristics of industrial scouring pads are generally mainly elastic grinding, which can effectively prevent excessive cutting and scratching the surface of the work piece; followed by cold cutting, the common structure is effective for heat dissipation, which can prevent discoloration and deformation caused by overheating of the work piece during processing; its The third is that industrial scouring pads can prevent clogging, water and oil resistance; during the grinding process, the fibers will continue to be lost, and new grinding ore will continue to form naturally, providing better processing quality for the work piece.
We distributes and wholesales various brands of Bonded Abrasives , Abrasive Sanding Disc, Cutting Wheels , Abrasive Flap Disc, Flap Wheels , Flap Disc Backing Pad, Flap Disc Adhesive , and Surface Conditioning Product etc, and enjoy a high position among consumers.


Abrasive Scouring Pad,Scouring Pad Rolls,Non Woven Hand Pad,Abrasive Scouring Pad Roll,Green Scouring Pad
Zhengzhou Jiading Abrasive Manufacturing Co.,Ltd , https://www.jd-abrasives.com












![<?echo $_SERVER['SERVER_NAME'];?>](/template/twentyseventeen/skin/images/header.jpg)